The CaTS Help Desk was recently made aware that yesterday afternoon a large number of Wright State faculty, staff, and students received an email from an Alexa Brown at Retirement Expert with a subject line of ‘Retirement And Pension Meetings for Wright State University Employees’ indicating eligibility to receive a free consultation for retirement benefits. Please be aware that this message originated from a third-party organization that is NOT affiliated with Wright State University.
Email Security

On this page:
- Anti-Spam Service (Microsoft Defender)
- Email Scan Alerts (Phishing)
- Email Bombing/Flooding
- Microsoft Defender Safe Links and Safe Attachments
- Email Security Alerts
Anti-Spam Service (Microsoft Defender)
Unsolicited commercial email, also known as spam, has become an increasing problem at the university. To reduce the amount of time involved with managing spam, CaTS is now offering a new anti-spam service called Microsoft Defender, which is available to faculty, staff, and students with @wright.edu email accounts. Microsoft Defender uses a spam evaluation system to determine if an email is legitimate, or should be classified as spam and placed in Quarantine.
Email Scan Alerts (Phishing)
Points to Remember
- CaTS will never ask you for your account information (username or password) in an email.
- If an email is difficult to read (poor grammar or wording), it is most likely a scam.
- If you receive an email about a problem with your account, do not click on any links or provide your username and password. Go directly to the site and log in.
- Do not follow any link in an email coming from an unknown source.
- Banks, credit unions, and other financial institutions will never ask for your account information in an email.
Recently there has been a large number of phishing attempts targeting Wright State University students, faculty, and staff. These attempts appear in the form of an email sent to a university inbox, and tries to get the user to "verify account information" by sending their CAMPUS username and password in an email, or clicking on a link within the email.
CaTS has developed this page to provide you with tips on how to keep your information safe from phishing attempts, and to alert you to any attempts you may see in your inbox. Please take a moment to review the "Points to Remember" section on the right for tips on how to protect your account information. Then, review the examples below showing the many recent scams targeting Wright State. If you receive an email that looks like any of these, do not reply to it or click on any of the links in the message.
If you have reviewed the information on this webpage and are still unsure as to the authenticity of an email you have received, please do not hesitate to contact the Help Desk at 937-775-4827 or 1-888-775-4827, or by email at helpdesk@wright.edu. We will help in any way we can to validate the email you've received.
Email Bombing/Flooding
Recently CaTS has noticed an increase in Wright State members who are targets of an IT security incident called 'email bombing'.
What is email bombing?
Email bombing is when an attacker registers your email address with hundreds or thousands of mailing lists.
Why was I targeted for email bombing?
The most likely reason someone is doing this to you is because they are trying to hack your account or overwhelm your inbox with messages so that you don't notice an important email about fraudulent activity. People who deal with financial data are more commonly targeted.
A lot of the emails I am getting have an unsubscribe button. Should I click it?
In general, we don't recommend trying to unsubscribe from mailing lists. Most reputable services that do mailings, won't email more than once unless you have confirmed your subscription. Less reputable services may unsubscribe you, but then sell your address to other services.
Can CaTS, Microsoft, or Google block these emails from being sent to me?
Unfortunately this is difficult because the attacker is not directly emailing you. Instead, the attacker is likely using a bot network of hundreds/thousands of IP addresses that are browsing to legitimate websites, entering your email address, and signing you up to receive a newsletter. Some people want to receive some of these newsletters so we cannot globally block them. We cannot block the emails based on the sender's IP address because they are coming from a legitimate newsletter website. We can block the emails based on keywords in the sender address, subject, or body of the email but we run the risk of blocking legitimate emails if we get the filters wrong.
Can I set up an email filter for these messages?
Below is an example of an Office 365 Inbox Rule that can be applied to your Wright State email during, and after, an email bombing attack:
During an Email Bombing Attack
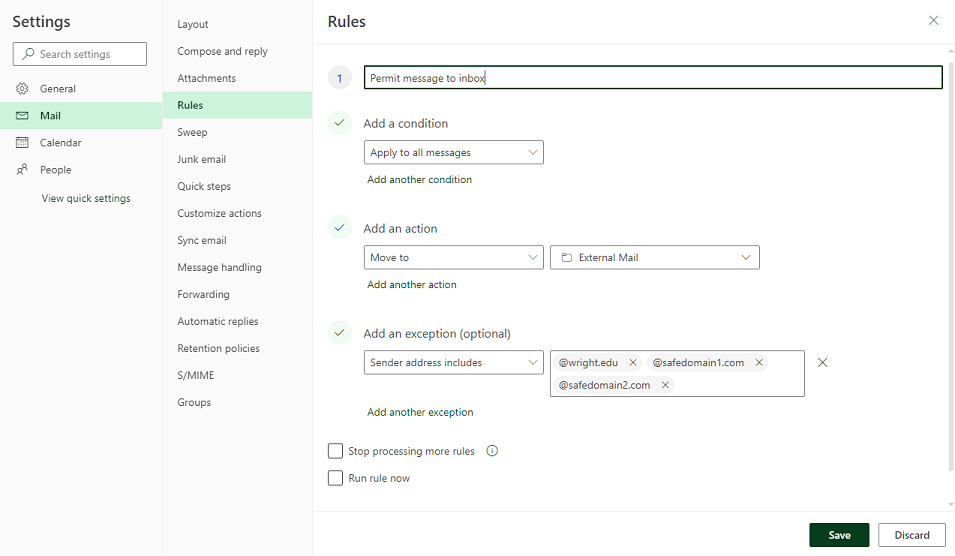
During the attack, you can set up a filter in Office 365 to move all emails sent from a specific address or domain to a singular folder, such as an 'External Mail' folder. This will keep your main Inbox free of these messages until the initial attack subsides:
- Log in to outlook.wright.edu using your Campus 'w' username and password
- Click on the gear icon in the top righthand corner, and click View all Outlook settings at the bottom of the menu
- Click on Mail > Rules > Add new rule
- Enter a name for the rule (ex.: Permit message to inbox) and set the condition to Apply to all messages
- Set the action to Move to, and then select the folder you would like the spam messages to be filtered into
- Add an exception to this rule to permit 'legitimate' emails from being filtered; CaTS recommends filtering by the sender domain, such as @wright.edu
- Click Save
After an Email Bombing Attack
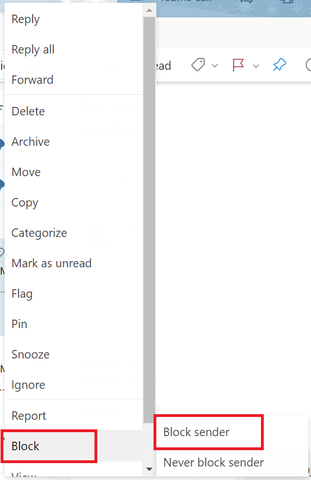
Once the initial attack begins to subside, CaTS recommends disabling the Office 365 filter and using the Block Sender functionality to address any additional messages you may receive.
Disabling a Filter in Office 365
- Log in to outlook.wright.edu using your Campus 'w' username and password
- Click on the gear icon in the top righthand corner, and click View all Outlook settings at the bottom of the menu
- Click on Mail > Rules
- Click on the radio button next to the rule you want to disable, and click Save
Block a Sender in Office 365
- Log in to outlook.wright.edu using your Campus 'w' username and password
- Right-click on the spam message in your Inbox, and select Block > Block sender
Microsoft Defender Safe Links and Safe Attachments
Safe Links
With Microsoft Defender Safe Links, all URLs in an email message are rewritten as 'safelinks.protection.outlook.com/?url=' addresses. When a user clicks a URL in an email message, the URL is redirected to Microsoft's URL validation service. If the URL is not known to be malicious, the user will be redirected to the original URL. If the URL is malicious, the website will be blocked in the browser.
If you click a URL and believe that the site is being blocked in error, call the CaTS Help Desk at 937-775-4827, or email helpdesk@wright.edu. The blocked URL will then be investigated further.
Safe Attachments
With Safe Attachments, Microsoft detects an email that contains a malicious attachment and strips the attachment to prevent phishing and targeted malware attacks. If you receive an email containing an infected attachment, Microsoft will filter out the email to protect your account from being compromised. Please be aware that while the attachment is being analyzed for malicious content, there may be a delay in delivery of a few minutes.
If you have questions about these Microsoft Defender services, please call the CaTS Help Desk at 937-775-4827, or email helpdesk@wright.edu.
Email Security Alerts
Notification of Non-University Sponsored Retirement Message
Important Information Regarding 'Email Bombing'
Recently CaTS has noticed an increase in Wright State members who are targets of an IT security incident called 'email bombing'.
What is email bombing?
Email bombing is when an attacker registers your email address with hundreds or thousands of mailing lists.
Why was I targeted for email bombing?